Services
Secure hostinganchor
ISO 27001 certified
We are proud to be to provide secure hosting services, catering to diverse digital projects across industries and budgets. Our ISO 27001 certification and partnerships with major cloud platforms allow us to offer managed services and private cloud hosting from state-of-the-art data centres. Our security measures, technical expertise, and round-the-clock support make us a reliable choice for businesses seeking robust hosting solutions.
Discover
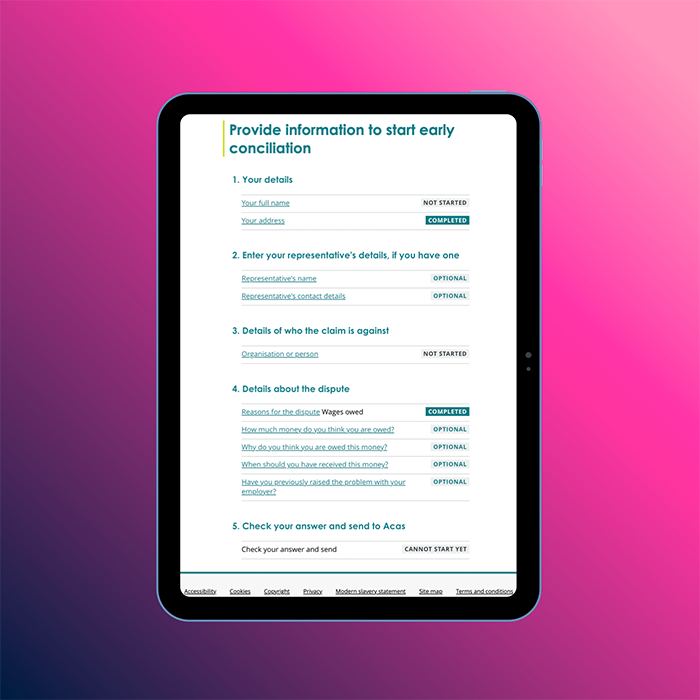
Government servicesanchor
Providing useful services to the public
Our experience with the UK government has been marked by a commitment to excellence in building transactional services and council websites that serve as vital community hubs. We've navigated GDS assessments with precision, assembling a team of experts to ensure compliance with service standards. Through user interviews, prototype iterations, and a multidisciplinary approach, we've crafted user-centric solutions that are accessible, intuitive, and continuously improved to meet evolving needs effectively.
Discover
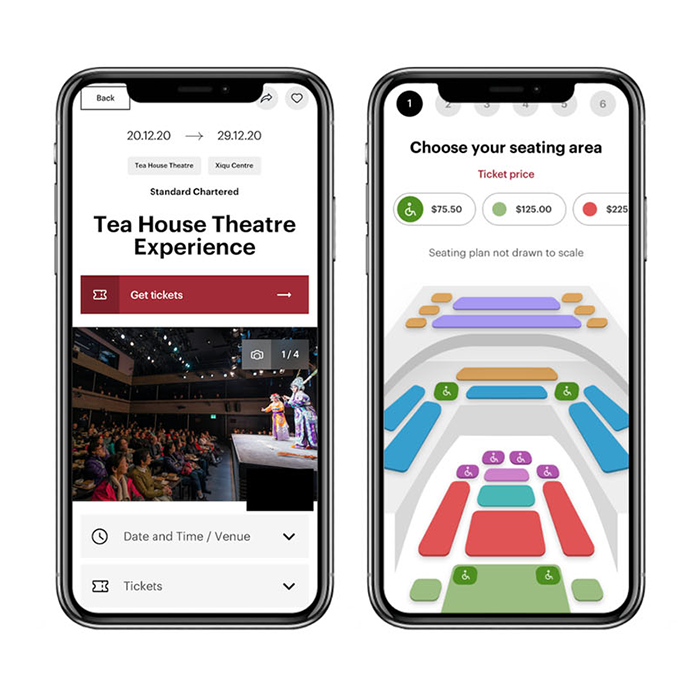
Creative experiencesanchor
User centred design and impactful solutions
Our company excels in delivering creative solutions thanks to our dedicated team of experienced UX designers and experts. With a deep understanding of user needs and industry best practices, our team crafts intuitive and engaging user experiences that drive results. By leveraging our expertise in user research, design thinking, and cutting-edge technologies, we ensure that every project we undertake is not just functional but also effective and delightful for the end user.
Discover
Digital transformationanchor
Building technically complex web solutions
Building technically complex web solutions is not just a task—it's a strategic journey guided by innovation, collaboration, and a relentless commitment to excellence. Through our expertise in the latest technologies, agile methodologies, rigorous testing practices, automated testing frameworks, extensible designs, and open-source ethos, we empower our clients to achieve digital success in an ever-evolving landscape.
Discover
Get in Touch
Got a similar project? Contact Us to discover how our team can help you transform your digital channels.